It’s no secret that Hunt A Killer games are full of codes, ciphers, and puzzles so we figured we’d write up a how-to guide since they can be intimidating at first!
To begin, let’s make sure we understand the difference between a cipher and a code. For most people, it’s as if you asked them what the difference is between mix and blend.
However, there is a difference between the two words. And even though code and cipher are often used interchangeably, the actual definitions for the words prove otherwise.
For instance, if a person came across a mysterious looking script, like the one shown below, more often than not, they would say, ‘Look! It’s a code.’
Ehvw ri oxfn zlwk doo wkdw brx vhhn! Dozdbv Wuhdvxuh wkh Dgyhqwxuh!
But is this a code? Or is it actually a cipher?
Let’s find out.
A code is a method of replacing a word or phrase with another word, phrase, or symbol, for an entirely different meaning. For example, ‘Take out the Trash’ could be code for ‘Meet me in one hour.’ This is also called a “cloak!”
Codes require a codebook. A code can produce a strong cipher, but if a codebook is lost or stolen, then decoding all communications is compromised until a new codebook is created. The codebook is essential for both those who are receiving the code and those who dispatch the code. Many codes were designed as a shorthand method of communicating.
Okay, so what about ciphers?
A cipher on the other hand, is an encryption system that is used to replace letters of a word. Ciphers are a means of distorting or hiding the true meaning of a message so that only the person who is aware of the system used for encryption is able to understand the message.
So, let’s look again at the mysterious script from above:
Ehvw ri oxfn zlwk doo wkdw brx vhhn! Dozdbv Wuhdvxuh wkh Dgyhqwxuh!
The apparent gibberish is most likely a cipher. To learn the message, it must be deciphered by reversing the system that was used to encode it.
In this case, we don’t need a codebook. Instead, we follow a series of instructions where we shift each letter by a certain number. The cipher requires one piece of shared information known as a key.
A code is often dispatched as something understandable to others who hear it, but it carries a secret message within those words for someone “in the know.” With a cipher, however, it’s often obvious to see that there’s a hidden message within that, when seen, carries no meaning to the naked eye (a cipher is not readable in its encrypted form). Its security comes from the system which hides it.
The Ciphers
(To construct the cipher alphabet, the letter A could be represented as any of the 26 letters. The letter B could be represented as any of the remaining 25 letters, C could be represented as any of the remaining 24 letters, and so on until the entire cipher alphabet has been formed. The total number of keys is therefore 26 x 25 x 24 x ... x 1 = 403,291,461,126,605,635,584,000,000).
The alphabet can be substituted with just about anything from letters and numbers, to hieroglyphics, from wingdings font to random images from the internet. You name, it you can use it as long as each letter has its own unique counterpart.
A Monoalphabetic Substitution Cipher is a cipher in which the cipher alphabet (either letters or symbols) remains unchanged throughout the message.
Each cipher alphabet is known as a key. If our message is intercepted by the enemy, who correctly assumes that we have used a monoalphabetic substitution cipher, they are still faced with the challenge of checking all possible keys, as there are over 400,000,000,000,000,000,000,000,000** combinations of letters in the American alphabet alone. If an enemy agent could check one of these possible keys every second, it would take roughly one billion times the lifetime of the entire universe to check all of them and find the correct one.
All the ciphers in the next three categories are types of monoalphabetic substitution ciphers.
Substitute Ciphers:
(A1Z26) Basic Alpha Number Substitution Cipher
The A1Z26 code is a very simple code known as a substitute cipher. There are 26 letters in the American alphabet; A would equal 1 and Z would equal 26 because it is the 26th letter in the alphabet.
HUNT A KILLER HINT: Look for a bunch of random numbers in a given document to help identify this cipher.
Atbash Cipher
The Atbash Cipher dates back even earlier (circa 500 BC) than the Caesar cipher, and was used for the Hebrew alphabet. Instead of shifting a letter to the right, it replaces the first letter of the Hebrew alphabet (aleph) with the last letter (tav) then the second letter (beth) for the second to last letter (shin), etc. So it uses a substitution where the letters are reflected instead of shifted.
If we used an Atbash-like cipher with our alphabet we would make a substitution like the following.
HUNT A KILLER HINT: Look for a string of random letters in the documents to identify this style of cipher.
Symbols
The alphabet can be substituted with just about anything, you name it, you can use it as long as each letter has its own unique counterpart. Here are a few samples:
Runes, Magic symbols and Alchemy:
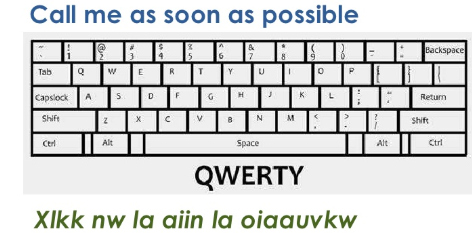
QWERTY
The Keyboard Cipher or Qwerty Cipher is a cipher that’s easy to spot when you know how. This is how it works: simply substitute each letter of the alphabet with the letter that is in the same place in the alphabet as it is on a keyboard or typewriter.
Shift Ciphers:
The shift cipher is one of the simplest and most widely-known encryption techniques. By shifting the alphabet a few positions in either direction, a simple sentence can become unreadable to casual inspection.
HUNT A KILLER HINT: Look for the word “Shift” or “Caesar” and a corresponding number in documents to identify this style of cipher.
Basic Shift
We can use any number of letters between 1 and 25 to shift the letter. This means that there are only 25 possible ways to decrypt any message using this simple shift method.
Caesar Shift Cipher - 3
The Caesar cipher is one of the earliest-known and simplest ciphers. It works in the same way as the shift cipher in which each letter in the plaintext is 'shifted' but a Caesar shifts 3 places down the alphabet. For example, with a shift of 1, A would be replaced by B, B would become C, and so on. The method is named after Julius Caesar, who used the 3-shift cipher in his private correspondences.
ROT13
ROT13 has several uses including in online forums as a means of hiding spoilers, punchlines, puzzle solutions, and offensive materials from the casual glance. It is the basis for many puzzles and games and is thought to be the equivalent of a magazine printing the answers to a puzzle upside down.
Like the Caesar, the ROT13 shifts a specific number of spaces, this time 13 spaces. As our alphabet has 26 characters (2×13) it is called a symmetric cipher. The Rot13 is also unique in that to encrypt and decrypt using the same key; for example, A → N and N → A.
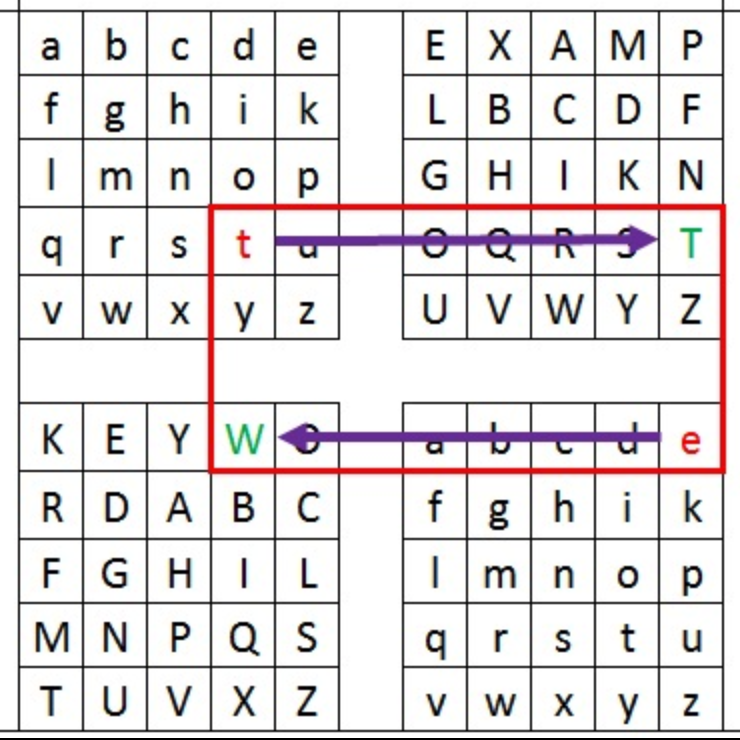
The Keyboard Shift
The Keyboard Cipher is a cipher that is easy to write, but hard to crack. It uses seemingly random letters. In reality, it’s kid stuff. This is how it works: simply take the letter you want to write, and shift it left, right, up or down one space on the standard qwerty keyboard, if you go right, X is C, and K is L. If you want to write a letter that is on the far left side of the keyboard, move to the far left, so L is A, P is Q, and M is Z.
Structured Codes:
Although all these codes can also be categorized in the substitute cipher category they are unique in that they use a structured symbolic alphabet that requires a codebook to decipher.
Morse Code
A century ago, one of the world’s first hackers used Morse code insults to disrupt a public demonstration of Marconi's wireless telegraph. Morse is constructed of dots and dashes that signify certain letters of the alphabet. Morse can be written like the example below or delivered in audio format.
.--- --- .. -. / ..- ... / ..-. --- .-. / ..-. .- -.-. . -... --- --- -.- / .-.. .. ...- . / --- -. / .-- . -.. -. . ... -.. .- -.-- / --... .--. -- / . ... -
Flag Semaphore
Before the invention of the telegraph, semaphore signaling from high towers was used to transmit messages between distant points.
Braille
Braille is another substitution cipher but it's not intended to keep things secret! Braille is specially designed for the blind and consists of a series of print letters using a grid of up to six raised dots. This enables the blind person to run their fingers over the dots in order to be able to read.
⠙⠊⠙ ⠽⠕⠥ ⠓⠥⠝⠞ ⠁ ⠅⠊⠇⠇⠑⠗ ⠞⠕⠙⠁⠽⠦
Pigpen
The Pigpen Cipher was used by Freemasons in the 18th century to keep their records private.
The alphabet is written in the grids shown, and then each letter is enciphered by replacing it with a symbol that corresponds to the portion of the pigpen grid that contains the letter.
For example:
Hidden In Plain Sight:
Acrostic
An acrostic cipher or code is when the first letter or syllable of every word, line, or paragraph spells out a secret message.
I love ice voraciously. Every instant nobody needs any, rabbits nest in armpits. Ice allows mean bullies entering senility to free rabbits in everyone's nerdy dreams. See, without ice, the hated meanies in seniority tweak everybody really terribly. Until me, nobody understood seniors!
Decoded: I live in Narnia. I am best friends with Mister Tumnus. (You’ll only understand this one if you’re a Chronicles of Narnia fan!)
Dot cipher (alt+803)
The dot cipher is a very sneaky way of hiding messages in plain sight. By adding a dot below the corresponding letter of the cipher, messages can be hidden in almost any style of text, from letters, to advertisements to newspaper articles. Want to make it a little more difficult? Use a pin prick instead!
Welcome to Hunt Ạ Kiḷler, an interactive story for you to expḷore through ịnveṣtigative meaṇs.
It is like yọur favoriṭe murder mystery TV shoẉ come to life in a real-world game wḥere every month is ạ new episode of the sṭory. Do you have what ịt ṭakeṣ for solvẹ thẹ ṃyṣtery?
Decoded: All is not what it seems.
Book code
A book cipher is a cipher in which the message is hidden in plain sight within a book or other form of text.
The most common book code key uses the page number, the line, and the word. 224.10.1 ; 187.15.1 ; 163.1.7 ; 309.4.4
Be aware, different editions of books might use different page numbers. To ensure the right book is used as a key, source the publication information, like edition, year published, and so on if possible.
Box Ciphers:
Although the this cipher sounds difficult, it’s really quite easy. To decipher the message, simply divide the code into four groups of four or more to fit the number of letters in the phrase, and rearrange them vertically, read from top to bottom row by row. Simple right?
Polybius Square
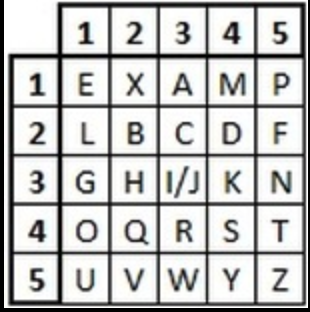
The Polybius Square is an ancient Greek invention, discovered by a historian named Polybius. It consisted of a 5x5 table or box where each square of the table is filled by a single letter. In the English alphabet of 26 letters, we have one too many letters. To get around this, we combine two letters, traditionally "i" and "j.” The table can be the standard alphabet or consist of a keyword (here the keyword is EXAMPLE).
Decryption is easy. Take the first two numbers of the code and find them on the grid reading across first and then down. For Example 2333 become HI
The tap code, sometimes called the knock code, uses the Polybius square as a form of communication commonly used by prisoners to communicate with each other.
The message is transmitted using a series of tap sounds with the listener only needing to discern the timing of the taps to isolate letters.
Each letter is communicated by tapping two numbers
the first designating the row (Down)
the second designating the column (Side-to-Side)
For example, to specify the letter "B,” you tap once, pause, and then tap twice.
Or to communicate the word "water,” the cipher would be the following (the pause between each number in a pair is smaller than the pause between letters):
Playfair Cipher
The Playfair Cipher was invented in 1854 by Charles Wheatstone, but became popular after an endorsement from Lord Playfair. The cipher encrypts pairs of letters, instead of single letters by using a box or table. The box consists of a 5×5 grid of letters that act as the key decryptor. As there are 26 letters in the alphabet, one letter of the alphabet (usually Q) is omitted from the table. The table can be the standard alphabet or consist of a keyword (in the example the keyword is playfair).
To decode, it’s important to know the three simple rules as to where each pair of letters are in relation to each other. The rules are:
If both letters are in the same column, take the letter below each one (going back to the top if at the bottom)
If both letters are in the same row, take the letter to the right of each one (going back to the left if at the farthest right)
If neither of the preceding two rules are true, form a rectangle with the two letters and take the letters on the horizontal opposite corner of the rectangle.
Four Square Cipher
The Four-Square Cipher was invented by the famous French cryptographer Felix Delastelle and is similar to the Playfair Cipher and the Two-Square Cipher. It uses four 5 x 5 grids or boxes, As there are 26 letters in the alphabet one letter of the alphabet (usually Q) is omitted from the table or combining "i" and "j" to get 25 letters. Two of the grids consist of the standard alphabet, and the other two grids contain a different keyword. In general, the upper-left and lower-right boxes are the "plaintext squares" and each contain a standard alphabet.
KEYWORD: Example Keyword = TWSP becomes TEST
Two-Square Cipher
The Two-Square Cipher is a variant of the Four-Square cipher and is much easier to use.
As with the Playfair and Four-Square cipher, the Two-Square cipher uses two square boxes of a 25 letter alphabet (dropping the letter Q) aligned either horizontally or vertically. Two unique keywords are used to form the boxes.
Directional Ciphers:
Rail Fence
The Rail Fence cipher (sometimes called zig-zag cipher) may look easy but it’s one of the most challenging to decode. Difficulty is also based on the number of rails or lines in the cipher.
It works by writing your message on alternate lines across the page, and then reading off each line in turn starting from the top.
Grids
Directional grid ciphers can come in any shape or form like the spiral below:
INWARD FROM BOTTOM-LEFT, COUNTER CLOCKWISE
PETIROVR··ECNAE····EFM····IRI····RUUMEXPEOWHATISY
Unlike a monoalphabetic cipher that uses fixed substitution over the entire message, a polyalphabetic cipher uses a number of substitutions at different positions in the message, making it stronger and almost impossible to break without a key!
Multilayer Ciphers
Vigenère Cipher
The Vigenère cipher was invented by Frenchman, Blaise de Vigenère in the 16th century. The Vigenère cipher is a method of encrypting alphabetic text by using a series of shift ciphers, based on the letters of a keyword. (Many use the Vigenère square to help decode messages).
Bob and Alice Cipher
An Alice and Bob cipher is a key exchange cipher designed to pass on messages without a third party being able to intercept the messages. One of the most popular Alice and Bob ciphers is the Diffe-Hellman Key Exchange.
Starting with modular arithmetic, Alice and Bob creates an equation that holds a private key and sends it to each other (Diffe-Hellman Key Exchange). They each extract the equation’s answer and use it to create a new equation. This new equation answer is the shared cipher key.
Here’s an illustration to help:
Other Mentionable Ciphers:
Pig Latin
In Pig Latin, words that start with a consonant sound switch that sound to the end of the word and add “ay.” This holds true for words that start with a cluster of consonants. Words that start with vowels just get “way” or “ay” added to the end of the word.
Consonant initial examples: pig = igpay; me = emay; too = ootay; wet = etway; hello = ellohay
Consonant cluster initial examples: glove = oveglay; shirt = irtshay; cheers = eerschay
Vowel initial examples: explain = explainway; egg = eggway; ends = endsay; eat = eatay
Binary
Convert messages to binary. Binary is the language of 1's and 0's used by computers. Combinations of these 1's and 0's can be enciphered and deciphered with a binary key, or by calculating the values represented by the 1's and 0's for each letter communicated in a message.
The name "Matt" would encipher to binary as: 01001101 01000001 01010100 01010100.
Ciphers and codes are so fun to do if you know how to approach them, and hopefully this guide serves as a starting point. Happy investigating!